Configuration
SecTrail MFA's configuration menu provides centralized management of applications, clients, mobile registration, and password reset operations.
Applications
Application profiles define which authentication methods users will use. Each client connects to an application, and the authentication factors determined within the application are applied.
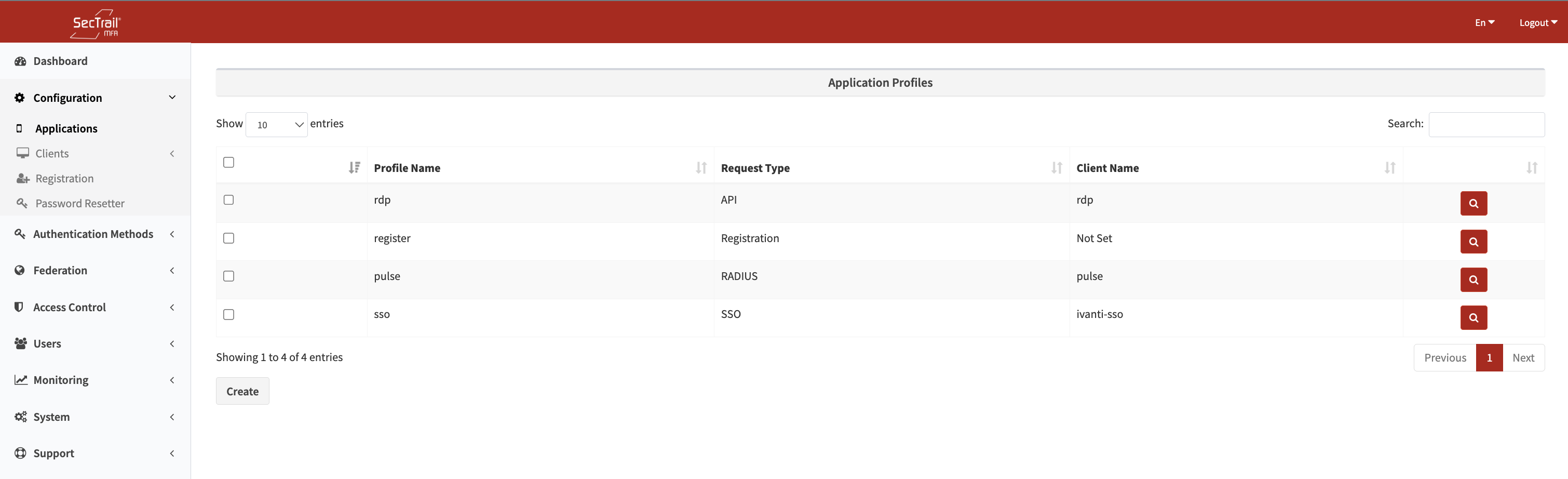
Application list page - View existing applications and create new application
Creating an Application Profile
Click the "Create" button from the list to create a new application profile. When creating an application profile, different profiles can be configured based on the request type. Each profile serves a specific function depending on the integration or authentication flow.
- API: Used for API-based requests. Typical use cases: RDP, ADFS, macOS login, Linux login, and external API integrations.
-RADIUS: Used for authentication requests coming through the RADIUS protocol.
SSO: Used for Single Sign-On (SSO) authentication flows.
Registration: A special profile used for user enrollment through the registration portal.
Authentication Factors
Configure authentication factors for each application:
Single Factor:
- Only one authentication method
- Example: LDAP, Local User, SMS OTP
Two Factor:
- Two different authentication methods
- Example: LDAP + Soft OTP, LDAP + SMS
Multi Factor:
- More than two authentication methods
- Example: LDAP + Soft OTP + WebAuthn
Profile Configuration
Authentication Methods:
- LDAP Authentication
- Local Authentication
- LDAP+OTP
- Soft OTP
- SMS OTP
- Mail OTP
- Push Notification
- Approved OTP
- Email Link
- Login with QR
- WebAuthn
First Match Rules:
With First Match Rules, you can dynamically route or assign authentication methods based on the first matching condition.

If multiple authentication methods are added to the same factor, First Match Rules determine which method will be applied first:
When First Match Rules are enabled, only the first matching authentication method is applied to the user. Once a match is found, the remaining methods are not evaluated.
When First Match Rules are disabled, all configured authentication methods are included in the flow. The user can attempt authentication using any of the available methods.
This mechanism ensures flexible and optimized authentication routing based on your configuration.
Clients
Clients represent different system and application types that connect to SecTrail MFA for authentication. Each client type has its own specific configuration requirements and use cases.
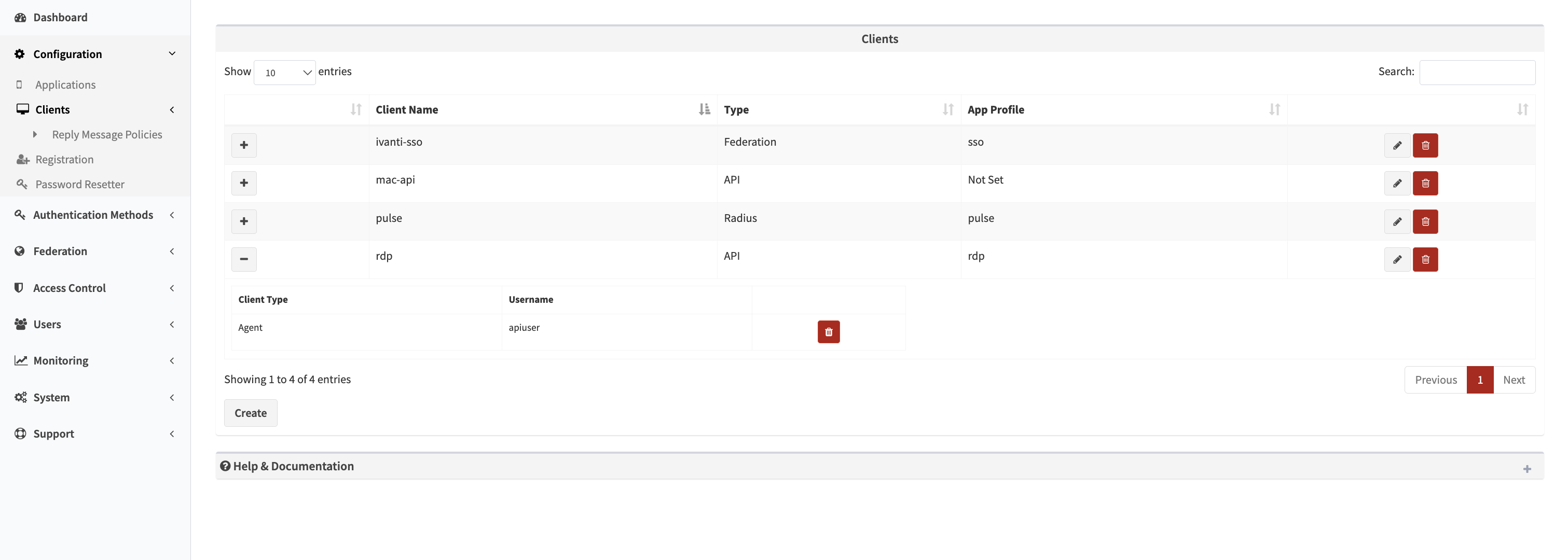
Client list page - RADIUS, API, and Federation client management
RADIUS Clients
Purpose: Network Access Server (NAS) devices that use the RADIUS protocol for authentication.
Click the "Create" button to add a new RADIUS client and configure NAS device details.
Configuration Fields:
Click the "Create" button from the list to add a new RADIUS client. Required information:
- Device Type: VPN, Firewall, Switch, Router, Wireless Controller
- NAS IP Address: IP address of the network device
- NAS Identifier: Unique identifier for the device
- Shared Secret: Pre-shared key for secure RADIUS communication
- Reply Message Rule: Custom reply messages based on authentication result
Common Usage:
- VPN gateways (Cisco ASA, FortiGate, Palo Alto)
- Network switches (Cisco Switches)
- Wireless access points (Aruba, Ruckus, Cisco WLC)
- Firewalls
Important Notes:
- Shared Secret must match on both SecTrail MFA and the NAS device
- NAS IP address is whitelisted for security
- Reply messages are shown to the user on VPN/WiFi login screen
API Clients
Purpose: Applications that integrate with SecTrail MFA through REST API using OAuth 2.0.
API clients are displayed in the Client List above. You can create new API clients from the "Create" button.
Client Types:
Agent Type (Machine-to-Machine):
- Machine-to-machine authentication for automated systems
- Client Credentials OAuth 2.0 grant type
- API access without user context
User Type (User-Based):
- API access with user credentials
- Password Grant OAuth 2.0 grant type
- API operations with user context
Configuration:
- Client ID: OAuth 2.0 client identifier
- Client Secret: OAuth 2.0 client secret
- Grant Types: Client Credentials or Password Grant
- Permissions: API endpoint permissions
Federation Clients (SAML Service Providers)
Purpose: SAML 2.0-based Single Sign-On (SSO) service providers.
SAML Service Providers are displayed in the Client List above. You can create new Federation clients from the "Create" button.
Configuration:
- Entity ID: Unique identifier for the service provider
- ACS URL: Assertion Consumer Service URL
- Metadata: XML configuration for SAML integration
- Certificates: SP public key certificate
- Attribute Mapping: User attribute mapping
SSO Sessions:
- Centralized session management
- Single Logout (SLO) support
- Session timeout configuration
- Active session viewing
Common Usage:
- Cloud applications (Office 365, Google Workspace, Salesforce)
- SaaS platforms
- Enterprise portals
- Custom web applications
Metadata Management:
- SP metadata import (XML upload or URL)
- IdP metadata export
- Automatic metadata updates
- Certificate rotation
Client Configuration Workflow
Create Client: Click the "Create" button and select the client type (RADIUS, API, or Federation)
Assign Application: Link the client to an Application profile that defines authentication factors
Configure Details: Click the + button to expand client details:
- RADIUS: Add NAS devices with IP, identifier, and shared secret
- API: Create OAuth clients with credentials (Agent or User type)
- Federation: Add SAML Service Providers with Entity ID and metadata
Manage Passwords: Use the eye icon button to show/hide sensitive information like shared secret
Edit/Delete: Use the pencil icon to edit or trash icon to remove configurations
Create Client → Assign Application → Add client-specific details (NAS/API/SAML) → Configure authentication factors in Application → Client ready for use
Registration Panel
Registration Settings configure the registration panel where users register their mobile devices for SoftOTP (Time-based One-Time Password) and Push authentication methods.
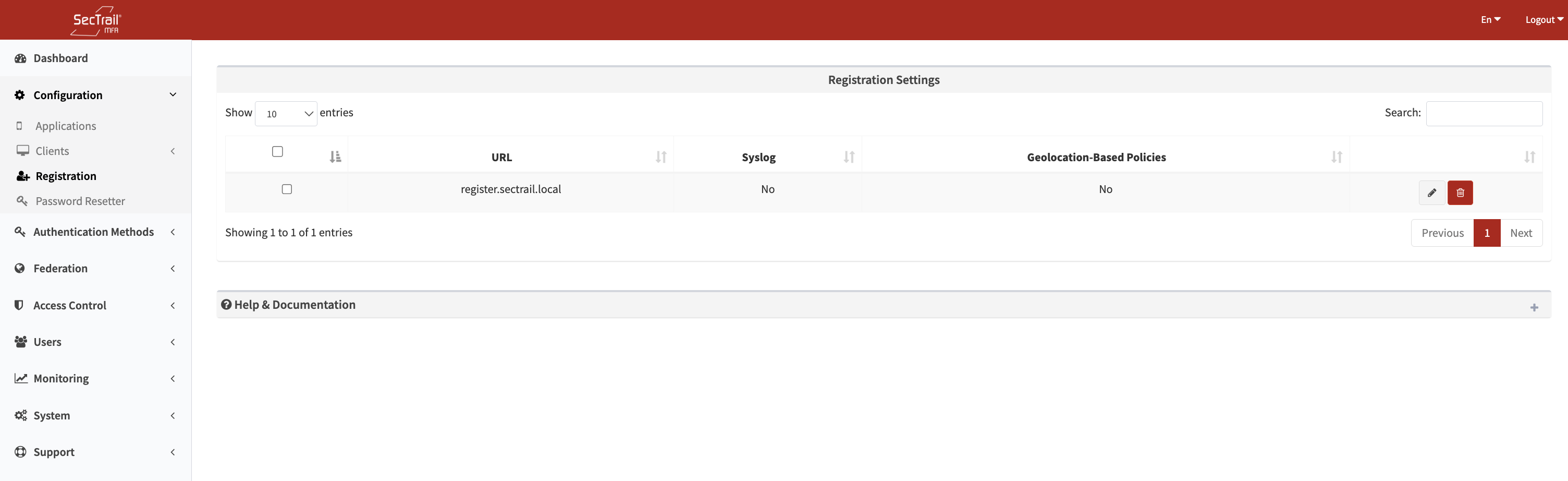
Registration settings form - URL, syslog profile, and geographic location configuration
Registration Panel Configuration
Registration Settings Fields:
URL (Required):
- Public domain where users will access the mobile registration panel
- Example:
https://register.company.com - This URL must be accessible to all users
- DNS records must be configured
Syslog Profile (Optional):
- Log registration events for auditing and monitoring
- All registration activities are sent to syslog
- Successful/failed registration attempts
- Device information and user information
Geographic Location Profile (Optional):
- Restrict registration panel access based on geographic location
- Country, region, IP range-based restrictions
- Block registration from suspicious locations
When using the mobile application, a domain must be configured to allow access to the registration panel, and necessary DNS records must be created. Domain information must also be specified in Registration settings.
Registration Application
After creating Registration Settings, you must create an Application of type Registration.
Registration Application Features:
- Authentication factors to be completed before viewing the QR code
- Usually LDAP or Local User authentication
- SMS or Email OTP can be added for additional security
How Users Register Their Mobile Devices
For detailed information on how users register their mobile devices, please refer to the Registration Panel section.
Password Reset
Password Reset Profiles enable self-service password reset functionality for users. Users can securely reset their passwords by completing PIN and Token authentication without administrator intervention.
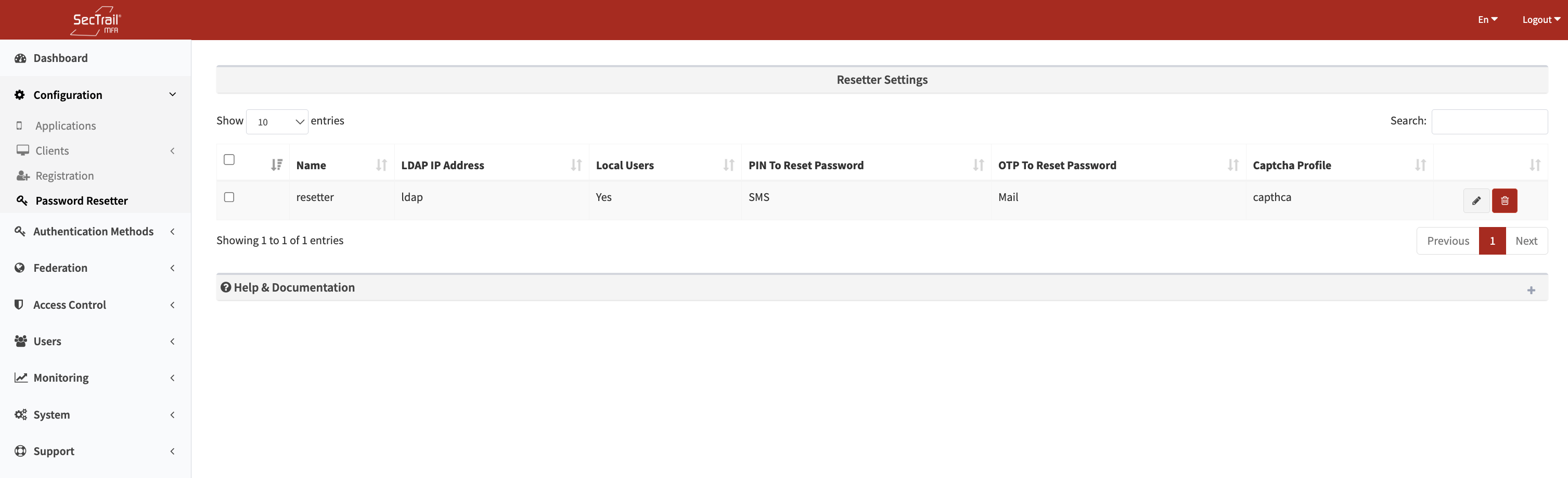
Password reset profile - LDAP server, PIN/Token methods, and captcha configuration
Password Reset Profile Configuration
Only one Password Reset Profile can be active in the system. This profile applies to all password reset requests.
Profile Configuration Fields:
Profile Name:
- Descriptive name for the password reset profile
- Example: "Self-Service Password Reset", "LDAP Password Reset"
LDAP Server:
- Select which LDAP servers support the password reset function
- Users authenticating through these LDAP servers can reset their passwords
- Multiple LDAP servers can be selected
- Active Directory, OpenLDAP support
Local Users:
- Enable or disable password reset for local authentication users
- Toggle with checkbox
PIN Code Configuration:
- Method Selection: Choose authentication methods to send PIN code
- SMS: Send SMS to user's phone number
- Email: Send to user's email address
- Both: User can choose
- Custom PIN Message Text: Custom text to appear in PIN code message
- Variables:
{pin},{username},{timestamp} - Example: "Your password reset PIN code is: {pin}. Code is valid for 5 minutes."
- Variables:
Token Code Configuration:
- Method Selection: Choose authentication methods to send Token code
- SMS: Send SMS to user's phone number
- Email: Send to user's email address
- Both: User can choose
- Custom Token Message Text: Custom text to appear in Token code message
- Variables:
{token},{username},{timestamp} - Example: "Your password reset confirmation code is: {token}. Code is valid for 5 minutes."
- Variables:
Captcha Profile (Required):
- Select a Captcha Profile
- Captcha Profile must be created with "Always Show" option enabled in Access Management → Captcha section
- Prevents automated password reset attempts
- Displayed on the initial reset page
- Provides bot protection
How Users Reset Their Passwords
Access Point:
Users access the Password Reset panel through the Registration Panel. After going to the registration panel, click the "Reset Password" button to start the password reset process.
Step-by-Step Password Reset Process:
AccessRegistration Panel
- User goes to the registration panel URL
- Example:
https://register.company.com
Click Reset Password
- User clicks the "Reset Password" button on the registration panel
- Redirected to password reset page
Enter Username/Email and Captcha
- User enters username or email address
- Completes Captcha verification (bot protection)
- Clicks "Submit" button
Receive PIN Code
- System sends a PIN code via selected method (SMS/Email)
- PIN code is valid for 5 minutes
- User checks SMS or email
Enter PIN Code
- User enters the received PIN code for verification
- Clicks "Verify" button
Enter New Password
- If PIN is correct, user is directed to password reset page
- User enters new password according to password policy rules
- Password requirements are displayed (minimum length, complexity)
Receive Token Code
- Before saving new password
- System sends a Token code via selected method (SMS/Email)
- Token code is valid for 5 minutes
Enter Token Code
- User enters the received Token code
- Clicks "Confirm and Save" button
Password Updated
- If Token is correct, password is successfully changed
- Success message is displayed
- User can now log in with new password
- Password is updated in LDAP/Active Directory
For password reset to work, ensure users have valid phone numbers or email addresses in their profiles. If using LDAP, this information is automatically pulled from LDAP.
Create Password Reset Profile → Select LDAP servers and authentication methods → Configure PIN/Token messages → Enable Captcha for security → Users can now safely reset their passwords
Best Practices
Application Configuration
- ✅ Meaningful Names: Give application profiles descriptive names
- ✅ Correct Factors: Choose the number of factors appropriate for security requirements
- ✅ First Match Rules: Use rules for dynamic profile assignment
- ✅ Testing: Test each application before production
Client Management
- ✅ Strong Shared Secrets: Use long and complex shared secrets for RADIUS
- ✅ IP Whitelist: Add only known NAS IP addresses
- ✅ API Key Security: Store client secrets securely
- ✅ Metadata Current: Keep SAML metadata up to date
Registration and Password Reset
- ✅ SSL/TLS: Use HTTPS for registration and password reset panels
- ✅ Captcha: Always enable captcha for bot protection
- ✅ Geo-Restriction: Block access from suspicious locations
- ✅ Log Monitoring: Regularly review registration and password reset logs