Windows TrustStore
SecTrail CM enables automatic management of trusted certificates (Trusted Root and Intermediate CA) by establishing agentless connections to Windows TrustStore.
SecTrail CM supports TrustStores running on Windows systems. You can perform automatic certificate deployment and management via WinRM protocol.
Use Cases
- Trusted Root CA Management: Centralized management of Root CA certificates
- Intermediate CA Certificates: Distribution of intermediate CA certificates
- Corporate PKI: Enterprise PKI infrastructure management
- Certificate Chain Management: Establishing certificate chain trust relationships
Connection Requirements
| Requirement | Detail | Description |
|---|---|---|
| Protocol | WinRM (Windows Remote Management) | Windows remote management protocol |
| Port | 5986 or 5985 | Secure WinRM port (recommended) |
| Authentication | Username and Password | Windows user authentication |
| Transport | NTLM or Kerberos | Windows authentication protocol |
| User Permission | Certificate Store management permission | Permission to add/remove certificates to TrustStore |
Automated Operations
SecTrail CM automatically performs the following operations on Windows TrustStore:
- Certificate Discovery: Listing existing TrustStore certificates
- Certificate Import: Adding trusted certificates to TrustStore
- Certificate Remove: Removing existing certificates from TrustStore
- Validation: Certificate validity and chain testing
Supported Certificate Stores
| Store Location | Description |
|---|---|
| LocalMachine | Machine-based certificate store |
| My | Personal certificates |
| Root | Trusted root CA certificates |
| CA | Intermediate CA certificates |
Configuration Steps
1. Creating Windows TrustStore User
Navigate to Automation > Device Users and create a user for Windows TrustStore.
2. Adding Windows TrustStore Device to SecTrail CM
Click Automation > Devices > Add New Device button and enter the following information:
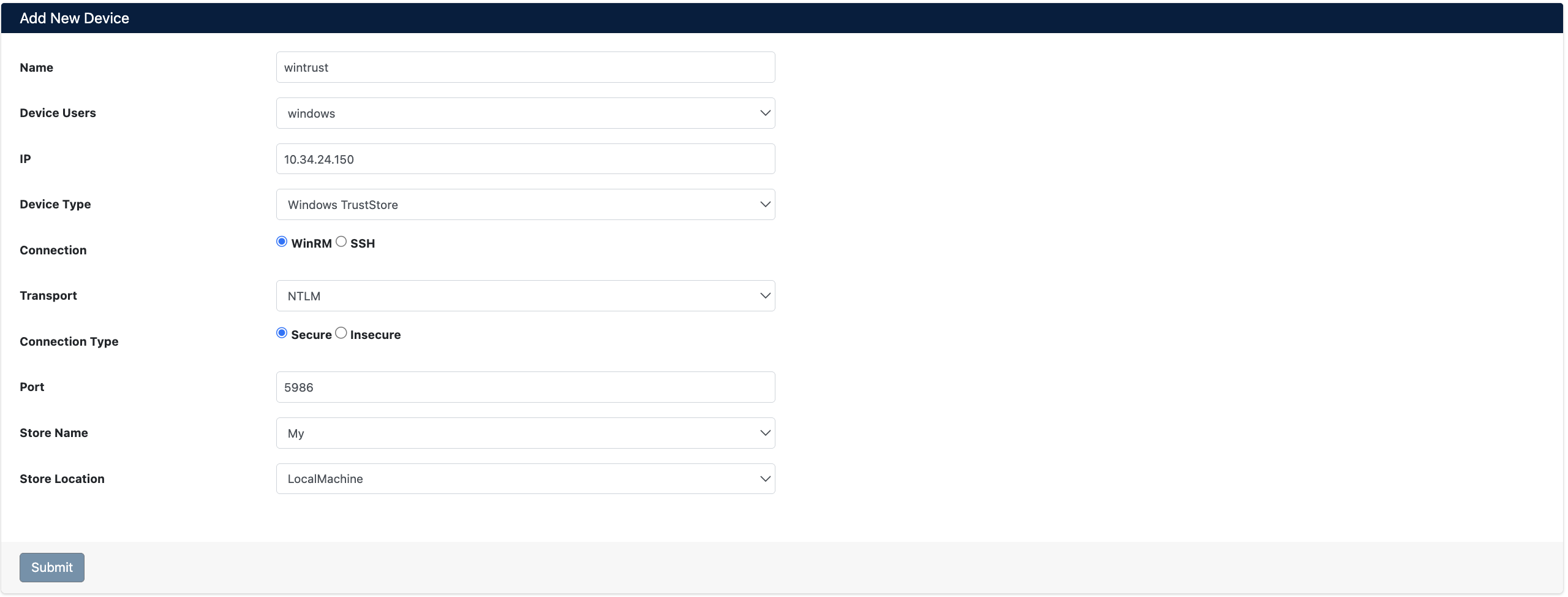
- Name: Provide a descriptive name for the device (e.g.,
wintrust) - Device Users: Select the user created in Step 1 (e.g.,
windows) - IP: Enter the IP address of the Windows TrustStore server (e.g.,
10.34.24.150) - Device Type: Select
Windows TrustStorefrom the dropdown menu - Connection: Select
WinRMorSSH(WinRM recommended for Windows) - Transport: Select
NTLM(or Kerberos) - Connection Type: Select
Secure(for HTTPS) - Port: Enter WinRM port (e.g.,
5986) - Store Name: Select store name (e.g.,
My) - Store Location: Select store location (e.g.,
LocalMachine)
After the Windows TrustStore device is added to SecTrail CM, certificates in the TrustStore are automatically included in the discovery period and scanned regularly. Automatic alarms are created for certificates that are about to expire or have issues.
3. Viewing Device Information
After the device is added, it will be displayed in the Automation > Devices list. Click on the row to view device details:
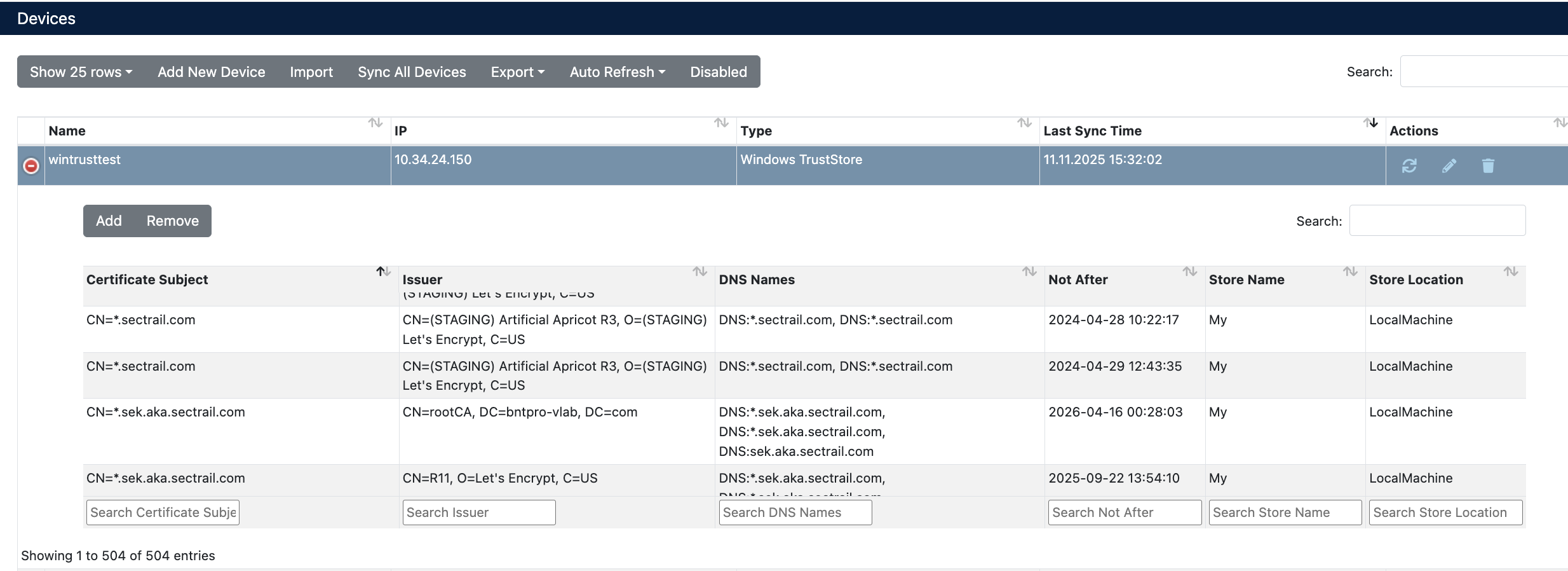
The following information is displayed in device details:
- Certificate Subject: Certificate subject information (CN, ST, L, O, OU)
- Issuer: CA information that issued the certificate
- DNS Names: DNS names defined in the certificate
- Not After: Certificate expiration date
- Store Name: Certificate Store name
- Store Location: Certificate Store location
Certificate Deployment
Step 1: TrustStore and Certificate Selection
- Select your Windows TrustStore device from Automation > Devices
- Click the Add button in device details
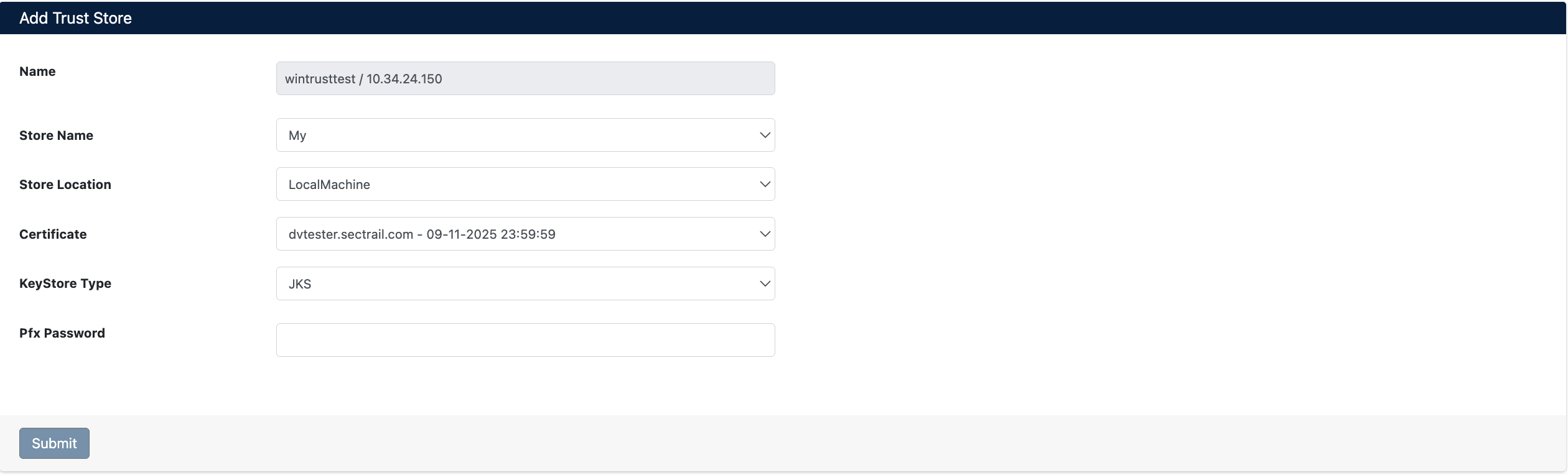
- In the Add Trust Store window that opens:
- Name: Provide a descriptive name for the certificate (e.g.,
wintrusttest / 10.34.24.150) - Store Name: Select store name (e.g.,
My) - Store Location: Select store location (e.g.,
LocalMachine) - Certificate: Select the certificate you want to add from the dropdown menu (e.g.,
dvtester.sectrail.com - 09-11-2025 23:59:59) - KeyStore Type: Select
JKS(or PKCS12) - Pfx Password: Enter certificate password
- Name: Provide a descriptive name for the certificate (e.g.,
Step 2: Starting the Deployment Process
Click the Submit button to start the certificate deployment process.
Step 3: Process Tracking
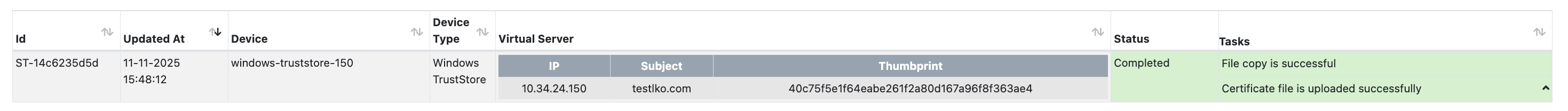
The deployment process can be tracked from Automation > Processes:
Operation Details
The following steps are performed during deployment:
| Step | Operation Description |
|---|---|
| 1 | Certificate file is copied to the server (File copy is successful) |
| 2 | Certificate is successfully uploaded to Windows TrustStore (Certificate file is uploaded successfully) |
Certificate Removal (Remove)
SecTrail CM supports certificate removal from Windows TrustStore.

Removal Operation Steps
- Select your Windows TrustStore device from Automation > Devices
- Click the Remove button in the row of the certificate you want to remove
- Confirm to start the removal operation
Removal Operation Task Details
The removal operation can be tracked from Automation > Processes. The following steps are performed during the operation:
| Step | Operation Description |
|---|---|
| 1 | Specified certificate is removed from Windows TrustStore (TrustStore Certificate Removed) |