IIS (Internet Information Services)
SecTrail CM enables automatic deployment and renewal of SSL certificates by establishing agentless connections to Windows IIS (Internet Information Services) web servers.
Connection Requirements
| Requirement | Detail | Description |
|---|---|---|
| Protocol | WinRM (Windows Remote Management) | Uses Windows Remote Management protocol |
| Port | 5986/ 5985 | HTTPS port recommended for secure connection |
| Transport | NTLM / Kerberos / CredSSP | Windows authentication mechanisms |
| Authentication | Domain account / Local Administrator | Windows user credentials |
Automated Operations
SecTrail CM automatically performs the following operations on Windows IIS:
- Certificate Store Import: Secure transfer of certificate and private key to Windows Certificate Store
- IIS Binding Update: Updating Virtual Server (Web Site) SSL bindings
- Configuration Backup: Backing up configuration before changes
- SSL Validation: HTTPS connection testing and validation
Configuration Steps
1. Creating IIS User
Navigate to Automation > Device Users and create a user for IIS:
- Windows domain user
- Or local administrator
2. Adding IIS Device to SecTrail CM
Click Automation > Devices > Add New Device button and enter the following information:

- Name: Provide a descriptive name for the device
- Device Users: Select the Windows user created in Step 1
- IP: Enter the IP address of the Windows IIS server
- Device Type: Select
IISfrom the dropdown menu - Connection: Select either
WinRMorSSH - Transport: Select either NTLM or Kerberos
- Connection Type: Select
Securefor secure connection - Port: WinRM port (default:
5986HTTPS or5985HTTP) - Trust Store: Include Trust Store?
DisabledorEnabled
After the IIS device is added to SecTrail CM, the IP addresses and ports of all Web Sites defined on the device are automatically included in the discovery period and scanned regularly.
3. Viewing Device Information
After the device is added, it will be displayed in the Automation > Devices list. Click on the row to view device details:
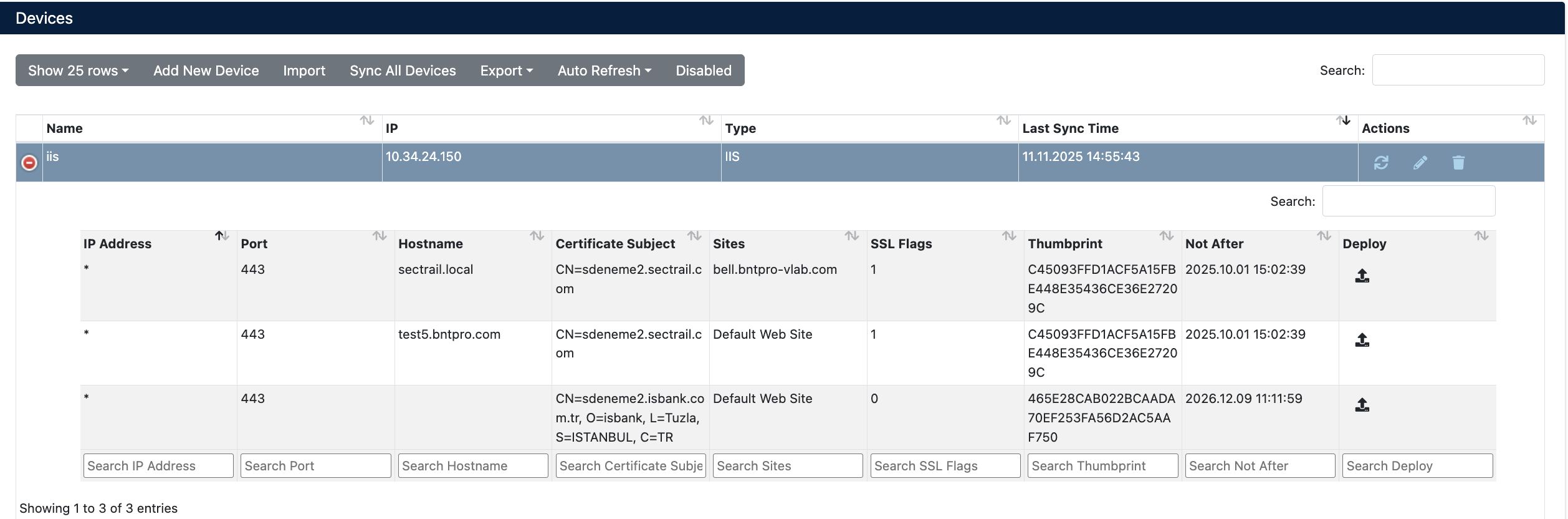
- IP Address: IP address of the IIS server
- Port: HTTPS port (443)
- Hostname: Hostname information of the IIS website
- Certificate Subject: Subject (CN) information of the current certificate
- Sites: IIS site name (Default Web Site or custom site name)
- SSL Flags: SSL flag value (0: no SNI, 1: SNI present)
- Thumbprint: Thumbprint value of the current certificate
- Not After: Certificate expiration date
- Deploy: For certificate deployment
Certificate Deployment
Step 1: Virtual Server and Certificate Selection
- Select your IIS device from Automation > Devices
- In the device details, find the Virtual Server (Web Site binding) where you want to deploy the certificate
- Click the Deploy button on the relevant row
- In the Deploy Certificate window that opens:
- Virtual Servers: Target Virtual Server information is displayed (Hostname, IP, Port)
- Certificate: Select the certificate you want to deploy from the dropdown menu
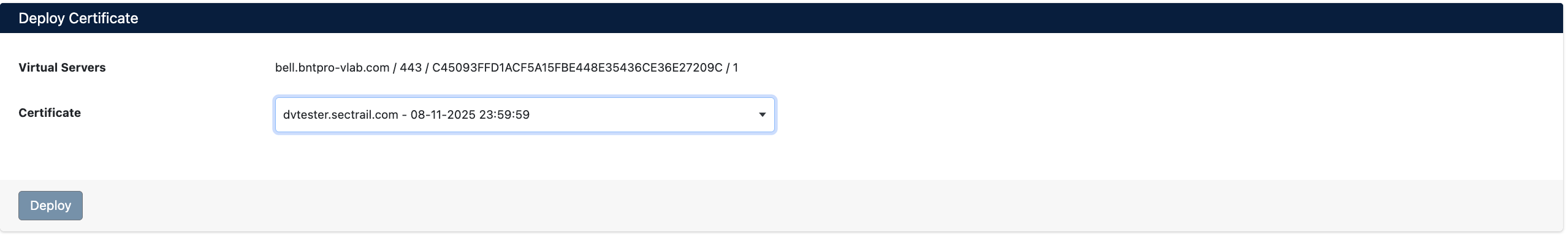
Step 2: Starting the Deployment Process
Click the Deploy button to start the certificate deployment process.
Step 3: Process Tracking
The deployment process can be tracked from Automation > Processes:
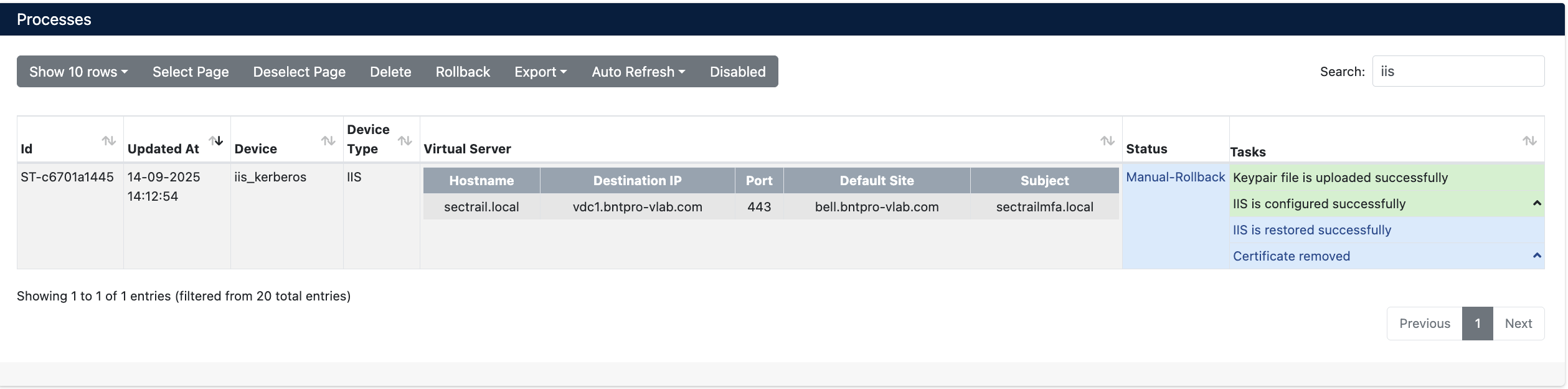
Operation Details
The following steps are performed during deployment:
| Step | Operation Description |
|---|---|
| 1 | Certificate is imported to Windows Certificate Store in PFX format |
| 2 | IIS website SSL binding configuration is updated |
Rollback Operation
The Manual Rollback feature can be used in case of issues after certificate deployment.
If an error occurs at any step during the deployment process, the system automatically performs a rollback and all changes are reverted.
Rollback Steps
- Navigate to Automation > Processes
- Find the operation you want to rollback
- Use the Manual-Rollback option in the Status column
- Confirm
Operations During Rollback
| Step | Operation |
|---|---|
| 1 | IIS website SSL binding is reverted to its previous state |
| 2 | Old certificate binding is restored |