Discovered Certificates
You can view, manage, and categorize all certificates found through discovery operations.
To view discovered certificates, you can use the following paths in the application panel:
- Discovery → Certificate-In-Use → Network List - Server-based view
- Discovery → Certificate-In-Use → Certificate List - Certificate-based view
Discovered Certificates List
You can examine discovered certificates in SecTrail CM in two different views:
- Certificate-Based List - Shows each unique certificate in a single row
- Server-Based List - Lists certificates according to the servers they're found on
Server-Based List View
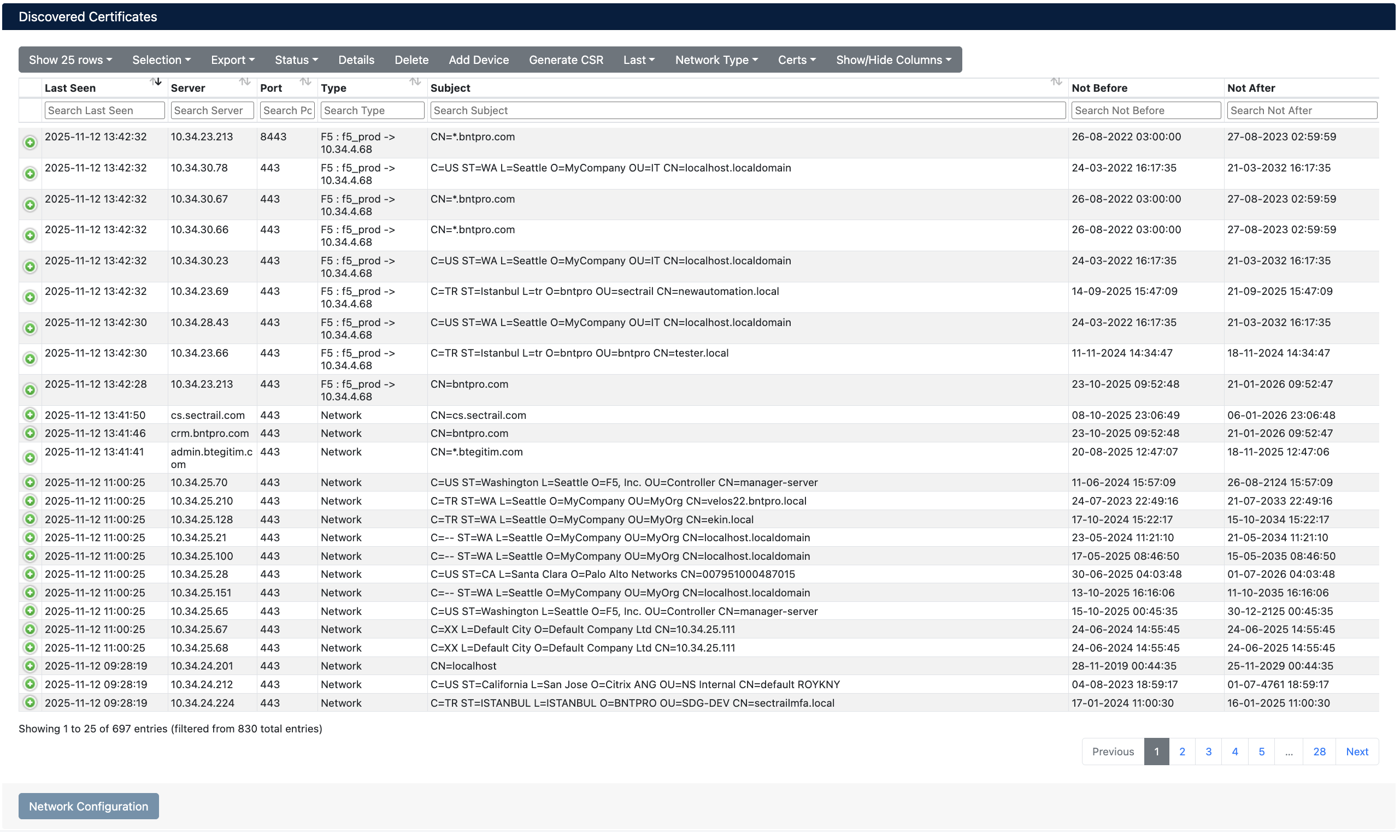
Discovered Certificates - Server-Based View
List Information
The following information is displayed for each row in the server-based view:
- Last Seen - Date and time the certificate was last seen
- Server - IP address or hostname of the server where the certificate is found
- Port - Which port the certificate is running on (e.g.,
443,8443) - Type - Network type of the certificate (
Network,External,F5, etc.) - Subject - Common Name (CN) information of the certificate
- Not Before - Certificate validity start date
- Not After - Certificate validity end date
- Status - License status of the certificate (
ManagedorMonitored)
Operations on the List
From the toolbar at the top of the page, you can perform the following operations:
- Show X rows - Set the number of rows to display per page (25, 50, 100)
- Selection - Select multiple rows for batch operations
- Export - Export the list (in Excel, CSV, PDF formats)
- Status - Filter by license status (
Managed,Monitored) - Details - View details of selected certificate
- Delete - Delete selected records
- Add Device - Add new device
- Generate CSR - Create Certificate Signing Request (CSR)
- Last - Filter by last seen time
- Network Type - Filter by network type
- Certs - Filter by certificate chain type (Server Certificate, Signing Certificate)
- Show/Hide Columns - Customize displayed columns
With the Show/Hide Columns button, you can customize displayed columns. You can add or remove columns according to your needs to use the list more efficiently.
Certificate-Based List View
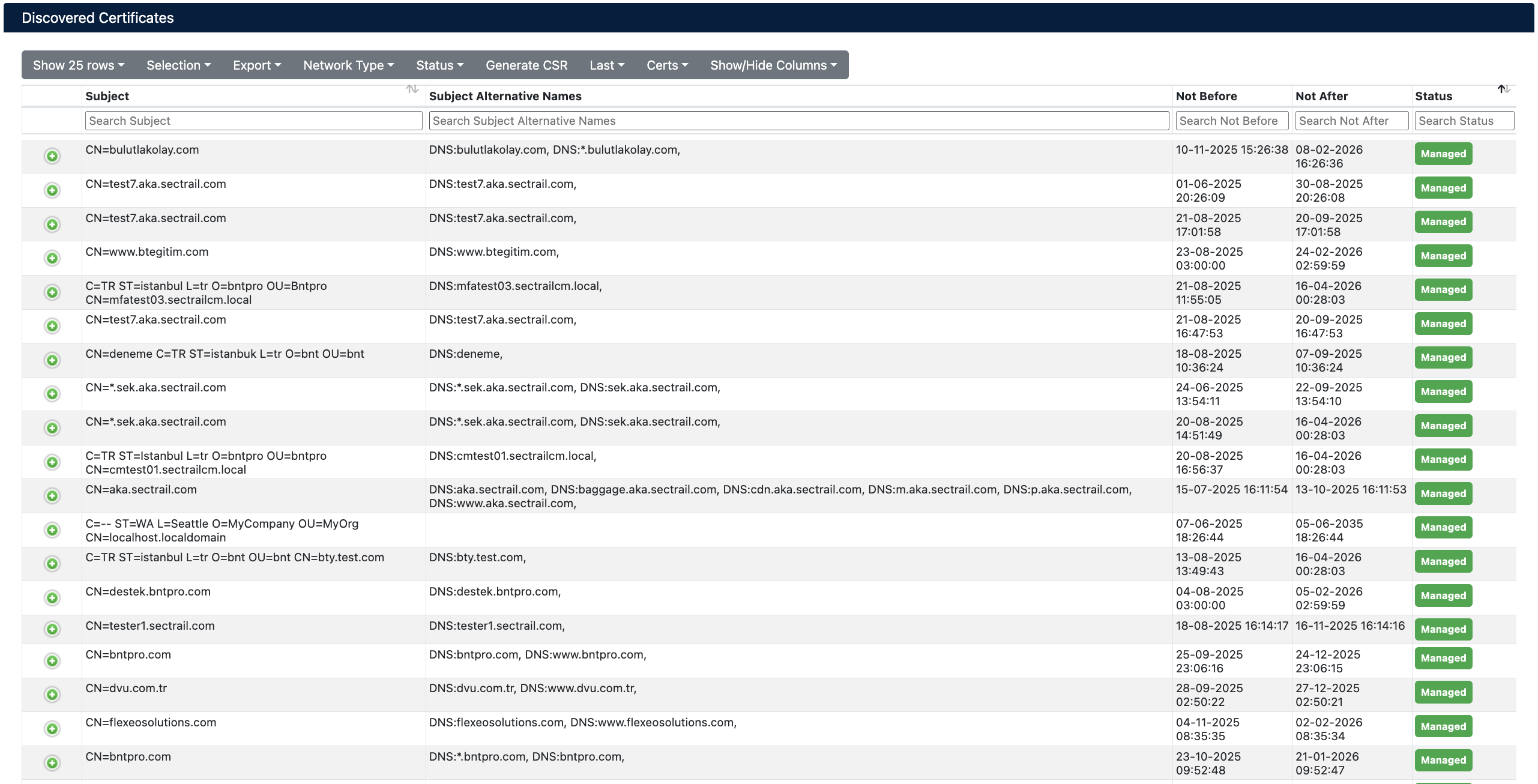
Discovered Certificates - Certificate-Based View
List Information
In the certificate-based view, each row represents a unique certificate and includes the following information:
- Subject - Certificate's Common Name (CN) and DN information
- Subject Alternative Names - Certificate's SANs (DNS names) list
- Not Before - Certificate validity start date
- Not After - Certificate validity end date
- Status - Certificate license status
Status (License Status)
There are two different statuses for discovered certificates:
| Status | Description | Usage Purpose |
|---|---|---|
| Managed | Certificates fully managed by SecTrail CM | Automatic renewal, deployment, lifecycle |
| Monitored | Certificates only displayed in inventory (read-only) | Provides inventory visibility, no alarms/warnings |
- Managed: Full control over certificates - create, renew, deploy, rotate operations possible
- Monitored: Inventory visibility only - certificates are displayed in inventory, but alarm, warning, and management operations cannot be performed
Network Configuration (Network Type Configuration)
Values in the Network Type column determine which network category the certificates belong to. These values can be customized with the Network Configuration feature.
You can access network type configuration settings from the Network Configuration tab found on the Discovery → Certificate-In-Use → Network List or Certificate List pages.
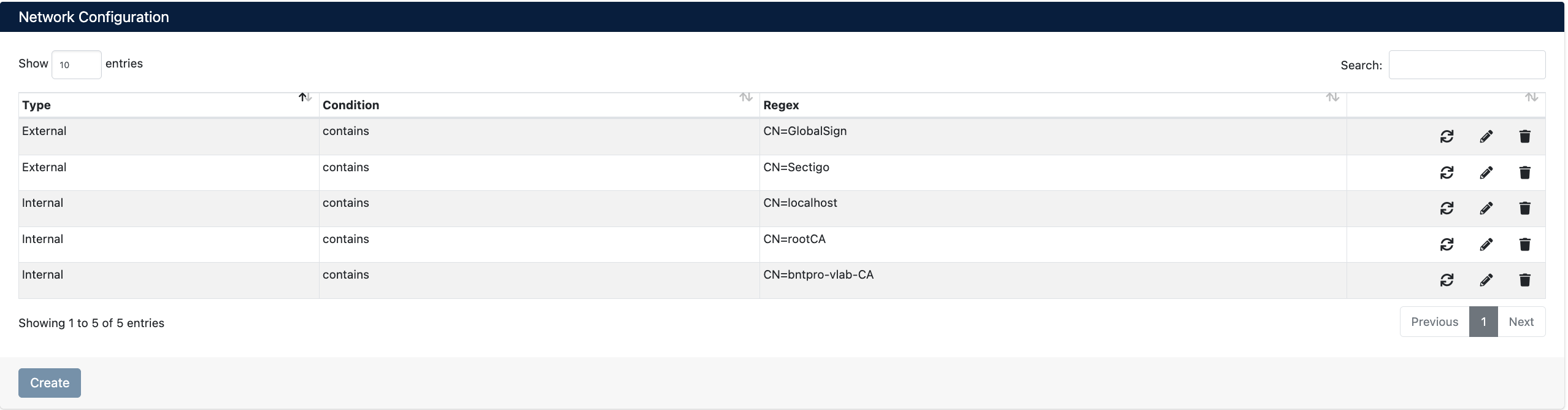
Network Configuration Management - Network Type Definitions
What is Network Configuration?
Network Configuration allows you to automatically categorize certificates based on Subject (CN) information. This way:
- You can automatically separate internal and external certificates
- You can group certificates belonging to specific Certificate Authorities (CA)
- You can make certificate reporting more meaningful
- You can speed up filtering and search operations
Network Configuration List
On the list page, you can see all defined network type rules:
- Type - Network type category (
External,Internal) - Condition - Matching condition (usually
contains) - Regex - Matching rule (text or regex to search within Subject)
Creating New Network Configuration
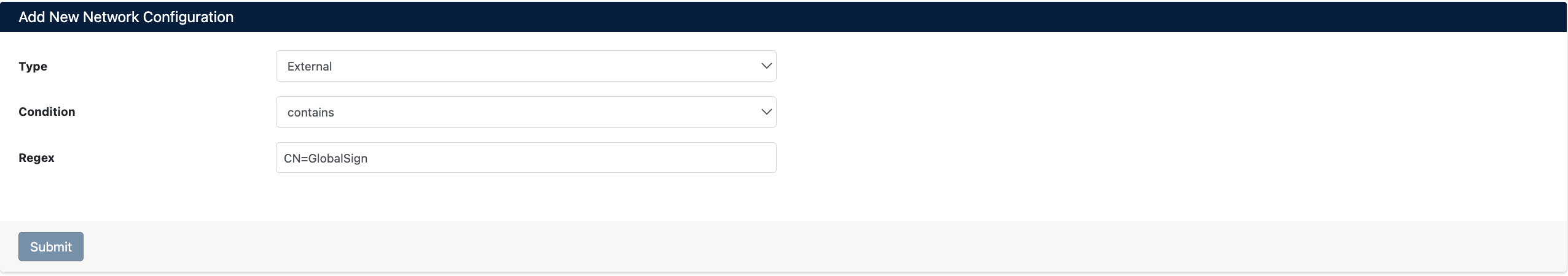
New Network Configuration Add Form
Configuration Parameters
| Parameter | Description | Options |
|---|---|---|
| Type | Determine network type | • External: External certificates (signed by public CAs) • Internal: Internal certificates (private CAs, self-signed) |
| Condition | Select matching method | • contains: Text searched in Subject (used in most cases) • equals: Exact match • regex: Regular expression matching |
| Regex | Enter text or regex pattern to search in Subject | • CN=GlobalSign (all certificates containing GlobalSign)• CN=localhost (localhost certificates)• CN=.*\.mycompany\.com (all subdomains under mycompany.com) |
After entering the form information, click the Submit button to save the configuration.
Viewing Certificate Details
You can view detailed information of a certificate by clicking on any certificate row or pressing the Details button:
- Subject DN - Full Distinguished Name information
- Issuer DN - CA that signed the certificate
- Serial Number - Certificate serial number
- Signature Algorithm - Signature algorithm (e.g., SHA256withRSA)
- Public Key - Public key information and algorithm
- Validity - Validity dates (Not Before / Not After)
- Extensions - Certificate extensions (SAN, Key Usage, etc.)
- Thumbprint - Certificate fingerprint (SHA1, SHA256)
When you define Network Configuration rules correctly, newly discovered certificates are automatically assigned to the correct categories and no manual action is required.