ACME - Automatic Certificate Management
SecTrail CM integrates with all Certificate Authority systems that support the ACME (Automatic Certificate Management Environment) protocol, enabling automatic ordering, renewal, and management of SSL/TLS certificates.
Supported ACME Providers
SecTrail CM is compatible with the following Certificate Authorities that support the ACME protocol:
- Let's Encrypt - Most popular ACME provider for free DV certificates
- Let's Encrypt Staging - Test server for test and development environments
- ZeroSSL - ACME service providing free SSL certificates
- Buypass - Norway-based free Certificate Authority
- Buypass Staging - Buypass test environment
- SSL.com RSA - SSL.com commercial certificates with RSA algorithm
- SSL.com ECC - SSL.com certificates with ECC (Elliptic Curve) algorithm
- Google Trust Services - Google's enterprise ACME service
- Google Trust Services Staging - Google test environment
- DigiCert - DigiCert ACME service (enterprise)
ACME protocol is an open standard (RFC 8555) that enables automation of the certificate lifecycle. This documentation will explain integration steps using Let's Encrypt as an example.
Connection Requirements
| Requirement | Detail | Description |
|---|---|---|
| Protocol | ACME v2 (HTTPS) | RFC 8555 standard |
| Authentication | ACME account registration | |
| Validation Methods | DNS-01, HTTP-01 | Domain ownership validation |
| DNS-01 Port | 53 (DNS) | Required for Domain Delegation (optional) |
| HTTP-01 Port | 80 (HTTP) | Required for HTTP validation (optional) |
| DNS Integration | PowerDNS, Akamai | Recommended for DNS-01 automation |
Automatic Operations
SecTrail CM automatically performs the following operations through the ACME protocol:
- ACME Account Registration: Creating an ACME account for certificate orders
- Certificate Order: Creating a new SSL/TLS certificate request
- Domain Validation: Domain validation via DNS-01 or HTTP-01 challenge
- Automatic DNS Record Management: Automatic creation and deletion of DNS validation records
- Certificate Issuance: Automatic retrieval of the certificate
- Certificate Renewal: Automatic renewal of certificates about to expire
- Certificate Deployment: Automatic addition of issued certificates to the system
Configuration Steps
1. Create ACME Account
Navigate to Integrations > ACME > Accounts and click the Register button:
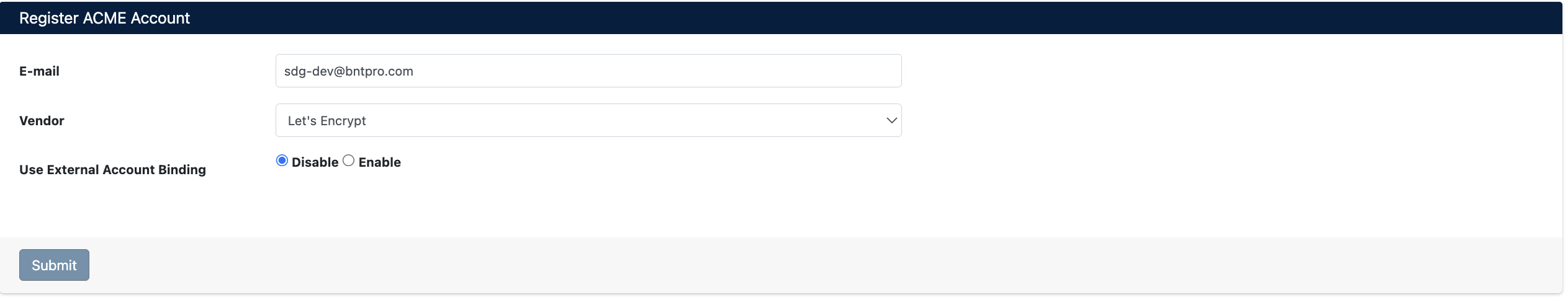
Enter the following information:
- E-mail: Email address for ACME account
- Vendor: ACME provider selection
- Let's Encrypt
- Let's Encrypt Staging
- ZeroSSL
- Buypass
- Buypass Staging
- SSL.com RSA
- SSL.com ECC
- Google Trust Services
- Google Trust Services Staging
- DigiCert
- Use External Account Binding: Required for some providers (default: Disable)
Click Submit button to create the ACME account.
When an ACME account is created, a key pair is automatically generated and registration is performed. Account information is securely stored.
2. View ACME Accounts
After adding an account, it will be displayed in the Integrations > ACME > Accounts list:
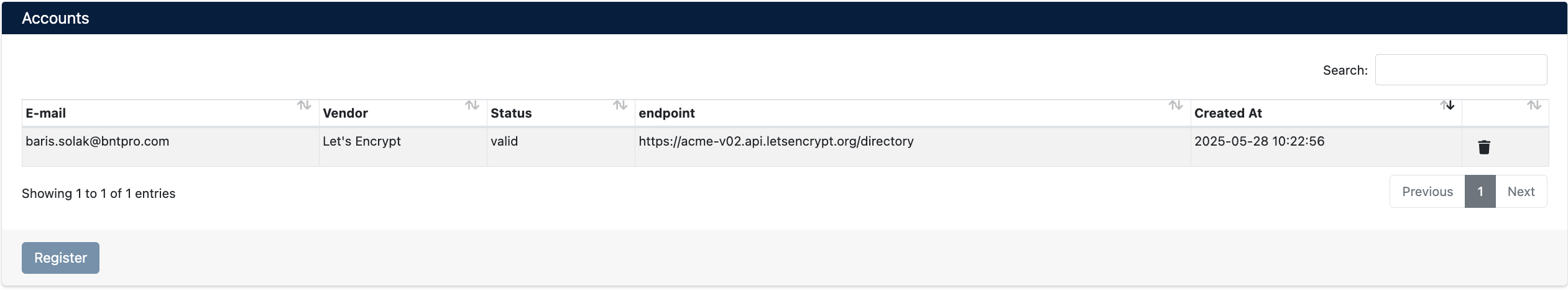
The list screen displays the following information:
- E-mail: ACME account email address
- Vendor: ACME provider being used
- Status: Account status (valid/invalid)
- Endpoint: ACME directory endpoint URL
- Created At: Account creation date
Account Operations
The following operations can be performed for each account:
- Delete: Delete the account
When an ACME account is deleted, all orders created with this account become invisible. However, issued certificates remain in the system.
3. Validation Methods
Two different validation methods are used when signing certificates with the ACME protocol:
DNS-01 Validation (DNS Validation)
You must use DNS validation method to sign wildcard certificates.
There are two different methods for DNS validation:
Method 1: Domain Delegation (Recommended)
Requirements:
- SecTrail CM application must have port 53 (DNS) open to the internet
- The
_acme-challengesubdomain of the domain to be signed must be delegated to the SecTrail CM server
Configuration:
Create the following NS record in your domain DNS:
_acme-challenge.domainname NS 3600 sectrailcm.server.address
Advantages:
- Fully automatic process
- No manual intervention required
- Ideal for continuous certificate renewal
Method 2: Manual TXT Record
Configuration:
For each certificate request, you must manually create a TXT record in your domain DNS:
_acme-challenge.domainname TXT 3600 TOKEN_VALUE
Disadvantages:
- Requires manual intervention for each certificate request
- Token value changes for each order
- Not suitable for automatic renewal
This method is not recommended as it requires manual intervention. Domain Delegation or External DNS integration should be used for automatic certificate renewal processes.
Method 3: External DNS Integration (Recommended)
Supported DNS Providers:
From the Integrations > External DNS section, you can configure one of the following DNS providers:
- PowerDNS - Open source DNS server
- Akamai - Enterprise DNS management
Configuration:
- Navigate to Integrations > External DNS
- Select your DNS provider
- Enter API credentials
- Test and save
Advantages:
- Fully automatic DNS record management
- TXT records are automatically created and deleted
- Ideal for wildcard and multi-domain certificates
- Full automation of certificate renewal
With PowerDNS and Akamai integrations, DNS validation records are fully automatically managed. No manual intervention is required, and certificate renewal processes run uninterrupted.
HTTP-01 Validation (HTTP Validation)
Use Case: Can only be used for single domain certificates. Not supported for wildcard certificates.
Requirements:
- Port 80 Access: The domain to be signed must respond to HTTP requests on port 80
- Public IP: The domain's public IP address must be able to receive requests
- Web Server: There must be a web server configuration for the domain
If Using F5 Load Balancer:
- The domain's public IP must route requests to F5
- You must know which virtual server it lands on
- Access to the
/.well-known/acme-challenge/path must be provided via port 80
ACME Challenge Process:
- ACME server sends an HTTP GET request to
http://domainname/.well-known/acme-challenge/TOKEN - Your web server must respond to this request with the validation token
- Once the token is validated, the certificate is issued
- Cannot be used for wildcard certificates
- Must be accessible via port 80 (not HTTPS)
- Separate validation required for each domain
- May require load balancer or firewall configuration
- For Wildcard Certificates: DNS-01 validation must be used (mandatory)
- For Single Domain: HTTP-01 or DNS-01 can be used
- For Automatic Renewal: DNS-01 with External DNS is recommended
- For Manual Process: HTTP-01 can be used
4. DNS Integration Configuration
External DNS integration must be configured to use DNS-01 validation.
DNS Challenge Records
When an ACME certificate order is created, TXT records are automatically created for DNS validation:
You can view challenge records in the Integrations > ACME > Acme DNS Domains section:
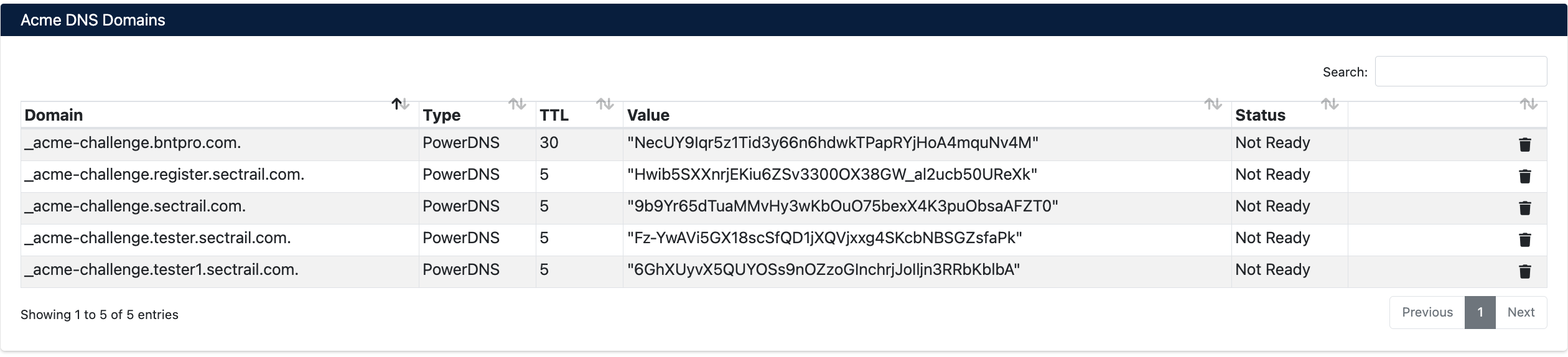
DNS Record Information
- Domain: Domain where the challenge record will be created (_acme-challenge.example.com)
- Type: DNS record type (PowerDNS, Akamai, etc.)
- TTL: Time to Live value (seconds)
- Value: ACME challenge token value
- Status: Record status (Not Ready, Ready, Valid)
DNS validation records are automatically added when a certificate order is created and automatically deleted after validation is complete. No manual intervention required.
DNS Record Statuses
- Not Ready: DNS record created, waiting for propagation
- Ready: DNS record propagated, validation can be initiated
- Valid: Validation successful, certificate issued
Create Certificate Order
To create a new certificate order via ACME:
Navigate to Integrations > ACME > Orders and click the Create ACME Order button:
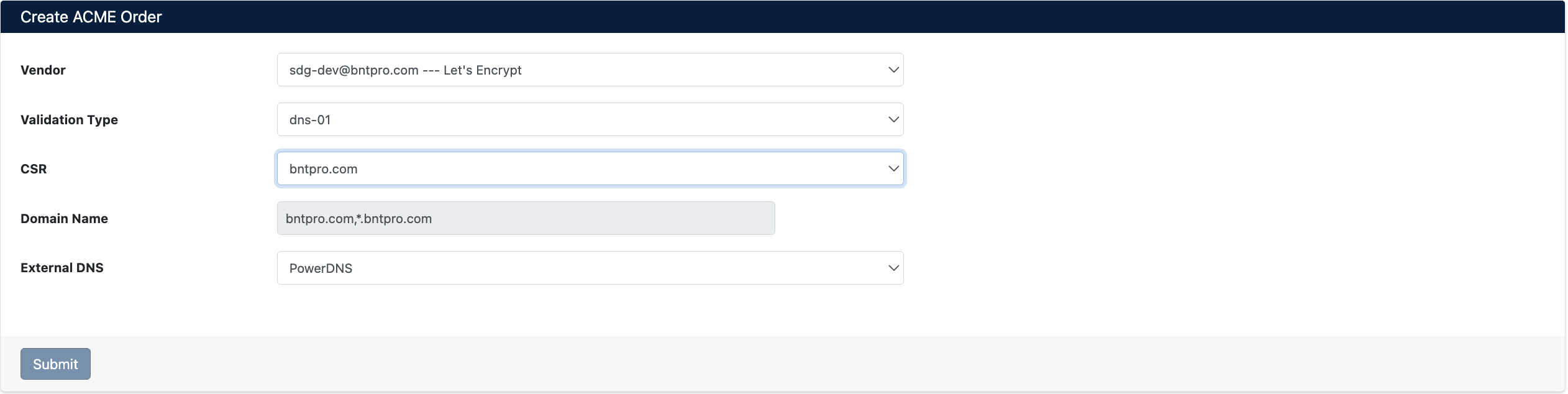
Order Information
Enter the following information:
- Vendor: ACME account selection (email --- vendor format)
- Validation Type: Validation method selection
dns-01: DNS validation (mandatory for wildcard certificates, recommended for single domain)http-01: HTTP challenge (only for single domain certificates)
- CSR: Certificate Signing Request selection
- Select from previously created CSRs
- CSRs can be created from the Integration section
- Domain Name: Domain names for the certificate
- External DNS: DNS provider selection for DNS validation (only for dns-01)
- PowerDNS, Akamai, Cloudflare, Route53, etc.
Click Submit button to create the order.
Before creating an order, you need to create a CSR from the Certificates > CSR section. CSR contains the required domain names, organization information, and public key for the certificate.
View Certificate Orders
To view your ACME certificate orders:
Navigate to Integrations > ACME > Orders:
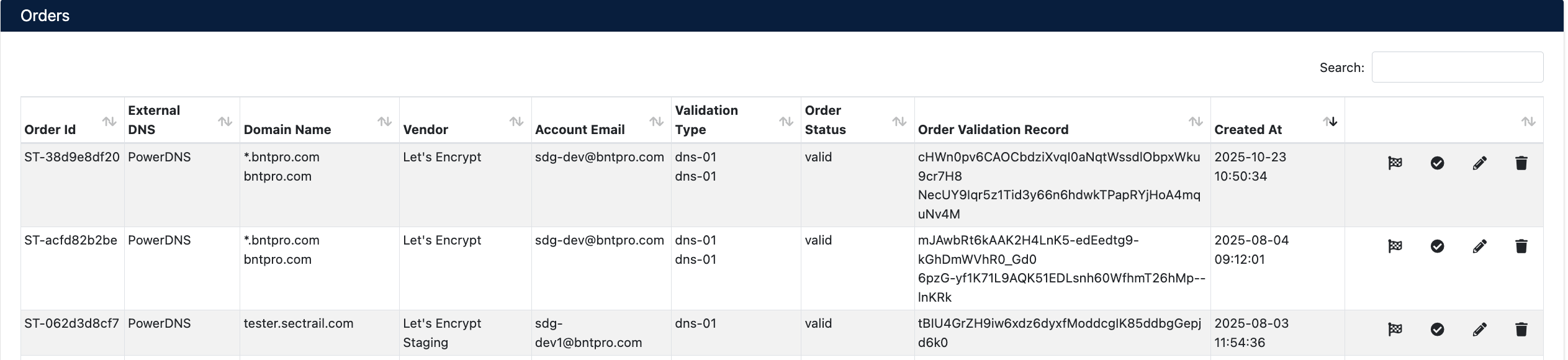
Order Information
- Order Id: SecTrail order ID
- External DNS: DNS provider being used
- Domain Name: Certificate domain names
- Vendor: ACME provider
- Account Email: ACME account email
- Validation Type: Validation method (dns-01 or http-01)
- Order Status: Order status (valid, processing, invalid)
- Order Validation Record: ACME challenge token values
- Created At: Order creation date
Order Operations
The following operations can be performed for each order:
- Refresh Order: Update order status
- Finalize Order: Retrieve certificate when validation is complete
- Download Certificate: Download issued certificate
- Delete Order: Delete order
Order Statuses
- pending: Order created, waiting for validation
- ready: Validation successful, ready to finalize
- processing: Certificate is being issued
- valid: Certificate issued successfully
- invalid: Validation failed
Certificate Lifecycle
1. Order Creation
- Create CSR (Certificates > CSR)
- Select ACME account
- Select validation type and External DNS
- Create order
2. DNS Challenge (Validation)
After order creation, automatically:
- DNS validation records are created (
_acme-challenge.example.com) - DNS propagation is awaited (typically 30-60 seconds)
- ACME server validates domain ownership
- When validation is successful, order status becomes "ready"
3. Certificate Retrieval (Finalization)
After successful validation:
- Click Finalize Order button
- Certificate is automatically issued
- Order status becomes "valid"
- DNS validation records are automatically deleted
4. Certificate Download
- Click Download Certificate button
- Certificate is automatically added to the system
- Can be viewed from the Certificates section
DNS validation record creation, validation, and certificate retrieval operations are fully automatic. No manual intervention required.
Certificate Renewal
ACME certificates can be automatically renewed:
- Select the certificate about to expire from the Certificates section
- Click Renew button
- A new ACME order is automatically created
- Validation and finalization occur automatically
Let's Encrypt certificates are valid for 90 days.