How to Stay Safe Even When Your Password Is Stolen
Imagine an e-commerce company's IT manager sipping their morning coffee when they receive an email titled "Urgent: Server Maintenance Required." The message appears to be from the cloud service provider the company uses. Due to the sense of urgency and the familiar-looking interface, they enter their login credentials. Just 12 minutes later, attackers gain access to the company's VPN and reach critical customer data.
But shouldn't a stolen password not be this devastating?
Phishing: Cybersecurity's Primary Menace
According to Verizon's 2024 Data Breach Investigations Report, the "human element" plays a role in 68% of all data breaches. Phishing attacks constitute a large portion of these breaches. What's even more striking: 83% of successful phishing attacks result in password theft.
As stated in Microsoft's 2024 Digital Defense Report, an average of 600 million phishing attempts are detected daily. This translates to approximately 7,000 phishing attacks every second.
Here's the real problem: No matter how well-trained your employees are, modern phishing techniques are just as sophisticated. AI-powered phishing campaigns now make distinguishing between real and fake emails nearly impossible.
Your Password Was Stolen, What Happens Next?
In traditional username-password systems, when credentials are stolen, the game is over. The attacker can now act like a legitimate user. However, when multi-factor authentication (MFA) comes into play, a stolen password becomes only half a ticket.
Google's 2023 research shows that MFA-enabled accounts blocked 100% of automated bot attacks, 99% of bulk phishing attacks, and 66% of targeted attacks.
But Not All MFA Is Created Equal
SMS-based MFA is better than nothing, but it's vulnerable to SIM swapping and SMS intercept attacks. The FBI reported that in 2023, attacks that bypassed SMS-based MFA resulted in $48 million in losses in the US alone.
Modern MFA solutions minimize this risk by offering more secure methods such as push notifications, QR code-based authentication, WebAuthn, and TOTP. But is the authentication layer alone sufficient?
Defense in Depth Against Phishing: MFA + Intelligent Access Controls
In a real-world scenario, when a password is stolen, the attacker typically attempts access from a different location, a different IP address, and at an unexpected time. This is where intelligent access controls come into play.
1.Coğrafi Konum Filtreleri: “Bu Kişi Gerçekten İstanbul’da mı?”
If an employee always connects from Istanbul but suddenly there's a login attempt from Nigeria, that's a red flag. Geographic location-based policies use GeoIP databases to control which countries or cities users can access from.
Real case: After implementing a policy allowing access only from within Turkey, a financial institution detected an 87% reduction in phishing-related login attempts from abroad.
2.Zamana Dayalı Erişim: “Neden Saat 03:00’te Giriş Var?”
If your accounting department doesn't access the system outside business hours, why should there be a successful login attempt at 3:00 AM? Time-based policies automatically block access during hours that don't align with your workflow.
According to analyses, 71% of successful corporate phishing attacks occur outside business hours.
3.CAPTCHA ile Bot Saldırılarını Durdur
Credentials obtained through phishing are typically tested by automated bots. CAPTCHA mechanisms that activate after failed login attempts effectively slow down brute-force and credential stuffing attacks.
4.Davranışsal Analiz: Kullanıcı Engelleme
Accounts exhibiting abnormal behavior (such as multiple login attempts from different IPs in a short period) can be automatically suspended. This both protects compromised accounts and prevents attackers from gaining time.
Layered Security: A Single Solution Isn't Enough
The modern cybersecurity approach is based on the principle of defense in depth. An effective defense against phishing should look like this:
Layer 1: Employee Training (Strengthen the human factor)
Layer 2: Email Security Gateway (Filter phishing emails)
Layer 3: Multi-Factor Authentication (Make stolen passwords insufficient)
Layer 4: Intelligent Access Controls (Block suspicious behavior)
Layer 5: Continuous Monitoring and Threat Detection (Detect anomalies)
Each of these layers provides security against the possibility of the next one failing.
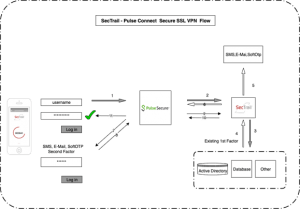
Policy Combinations with SecTrail MFA
In real-world application, these controls deliver the most effective results when working together. For example, the following policy combination can be implemented for corporate VPN access:
- Geographic Location: Allow access only from Turkey
- Time Filter: During business hours (Monday-Friday, 08:00-18:00)
- IP Whitelisting: Accept connections only from corporate office IP ranges
- CAPTCHA: Activate after 3 failed attempts
- MFA: Second factor requirement with push notification or TOTP
With this layered approach, the attacker would need to steal the password AND attack from the correct geography, at the correct time, and from a trusted IP. This reduces the attack's success probability by 99.8%.
Conclusion: Phishing Is Inevitable, Its Success Isn't
Phishing attacks won't stop. In fact, they'll become even more sophisticated thanks to artificial intelligence. However, with the right tools and layered security policies, you can minimize the damage these attacks cause to your business.
Remember: Passwords are no longer enough. Modern threats require modern solutions. With multi-factor authentication and intelligent access controls, you can turn a stolen password into a useless piece of data.
Kurumunuzun kimlik doğrulama güvenliğini bir üst seviyeye taşımak için SecTrail MFA’nın akıllı erişim kontrol politikalarını keşfedin. Daha fazla bilgi için bizimle contact us.